Power at risk: the cybersecurity threat facing renewables
High-profile incidents disrupting energy infrastructure, such as the attacks on the Nord Stream gas pipelines and anchor dragging incidents, have made asset security top of mind for the renewable energy sector. Questions and concerns from companies around global supply chain risk abound.
In response to these increasing physical threats, we commissioned an independent survey, in partnership with Cyber Energia. Our global energy advisory lead, Adrian Del Maestro, global offshore wind lead, Dawn MacDonald and Cyber Energia’s business development lead, Darrel Ellis discuss the findings and offer a fresh perspective on cybersecurity in the renewable energy sector.
Our jointly commissioned survey solicited thoughts from business leaders to assess the impact cyberthreats have on investment and operating strategies. The research captured insights from senior financial and operational leaders, asset managers, developers and technology providers, such as Gore Street Capital and Gresham House.
Results illuminate how cybersecurity is viewed as a business risk: shaping investment, governance and resilience strategies across the energy sector and beyond. Moreover, the survey results illustrate how businesses in renewable energy will need to do much more to improve cyber resilience if we are to mitigate the risk of the ‘lights going out’ in an increasingly complex geopolitical landscape.
Key data findings
Cybersecurity investment: Despite growing risks and concerns, investment levels remain low, and corporate response is reactive.
- The majority (95 percent) of asset owners interviewed allocate only 1–2 percent of annual revenue to cybersecurity, integrating it into broader risk management rather than treating it as a standalone priority. Companies would be well advised to address shortfalls in spending, considering the potential impact. Cyberattacks, such as ransomware, can disrupt operations for weeks or even months, potentially resulting in losses of millions.
- One in 10 companies surveyed stated they had already suffered a cyberattack, highlighting the immediate and growing risks facing the industry.
- Respondents note that regulatory compliance is becoming more demanding, requiring stricter supplier risk management with mandates such as:

1 in 10 companies surveyed stated they had already suffered a cyberattack.
- The Network and Information Security (NIS2) Directive in the European Union (EU), an EU directive expanding cybersecurity rules for critical sectors, including energy, with stricter risk management, reporting and penalties.
- The North American Electric Reliability Corporation (NERC) Critical Infrastructure Protection (CIP), a North American cybersecurity framework requiring utilities to protect critical power infrastructure from cyber threats through strict security controls and compliance measures.
- The Cyber Security Act (Australia), which imposes mandatory cyber risk management and incident reporting on critical infrastructure sectors.
- The United Kingdom’s (U.K.) Network and Information Systems (NIS) Regulations.
Supply chain insecurity: A major area of vulnerability likely to worsen.
- Seventy percent of respondents believe cyber threats will significantly worsen in the near future and cite supply chain vulnerabilities as a top concern.
- Respondents raised concerns about over-reliance on foreign suppliers for essential components such as turbine hardware and SCADA-related software. This leads to perceived risks of embedded threats — such as compromised sensors or remote-control mechanisms. These threats may in turn trigger greater government and regulatory scrutiny.
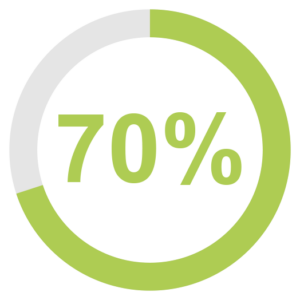
Seventy percent of respondents believe cyber threats will significantly worsen in the near future and cite supply chain vulnerabilities as a top concern.
There is an over-dependence on Asian manufacturers for essential components, leading to a supply chain imbalance.
Asset manager, solar investor – from AECOM / Cyber Energia survey
There is also increasing concern about single-control architecture, where operations and maintenance (O&M) providers or manufacturers retain sole access to digital controls. A breach in such a system could paralyze operations and trigger widespread distrust of the renewable model itself.
Legacy infrastructure and artificial intelligence (AI): New risks proliferating fast.
-
- Today’s energy systems — remote access, AI-driven control and automation — are interconnected for efficiency, but introduce new vulnerabilities and potential access points to broader networks. Legacy renewable assets are particularly exposed to cybersecurity threats, as they lag behind today’s digital advancements:
- Modern cyber attackers are leveraging AI and automation. 96 percent of respondents report that automated and AI-enhanced cyberattacks are now a growing concern. These threats bypass traditional defenses and exploit predictable response patterns. Conversely, the same AI technologies enhancing forecasting and operational efficiency are being weaponized by attackers. Malicious actors can use AI to learn network typology, connect SCADA systems and identify vulnerabilities. By using AI to learn systems, attackers can mimic normal traffic so malware blends into regular conditions.
- Despite this, only 18 percent of companies regularly upgrade critical network security equipment, such as routers and firewalls. This underinvestment can create exploitable backdoors across critical infrastructure. Insurance providers are beginning to deny coverage or impose steep premiums on organizations without sufficient cybersecurity maturity.
Renewable energy installations have been built for over a decade now. Obviously, the level of cybersecurity installed on 2012 assets is not the same standard deployed for assets which have been recently connected.
Asset manager, energy investor p from AECOM / Cyber Energia survey
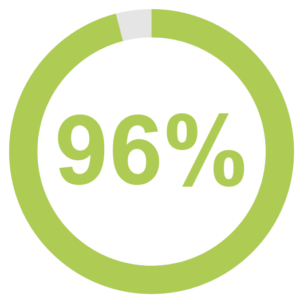
96 percent of respondents report that automated and AI-enhanced cyberattacks are now a growing concern. These threats bypass traditional defenses and exploit predictable response patterns.
Implications
Despite awareness of rising threats and one in 10 companies reporting past cyberattacks, many low-carbon developers admit to underinvesting in cybersecurity. This presents a risk to asset and system resiliency.
With increasing digitization and AI integration, cybersecurity must be elevated to the boardroom as a strategic risk, rather than in the traditional support function.
The cyber integrity of global supply chains poses a complex challenge. Developers rely heavily on suppliers for components and services. However, in many cases, O&Ms and equipment providers maintain exclusive control over digital infrastructure. Without secure contract models and shared governance, a single breach could compromise an entire portfolio of systems. It is essential for new assets to be future-proofed for AI-driven threats as well. This requires the entire sector to redefine “resilience”.
Mandatory incident reporting under NIS 2.0 marks an industry-wide movement toward greater transparency. Historically, organizations have not been required to report cyberattacks, making it difficult to understand the true scale of incidents within the renewable energy sector. Due to concerns about brand reputation, insurance implications and stakeholder perception, many attacks are believed to go unreported. However, new regulations now mandate timely and transparent reporting, fostering greater accountability at the executive level.
Recommendations
Government
Energy security is now a strategic pillar for national interest. As countries balance decarbonization with reliability, it is important that governments set and enforce rigorous cybersecurity standards for the energy sector.
NIS 2.0 sets a legal precedent. Governments must manage compliance and introduce real consequences for inaction. Additionally, it is essential that backdoor disclosures, vendor audits and DevOps Research and Assessment (DORA) frameworks be extended to the entire energy ecosystem, beyond financial institutions alone.
As we look at the rapidly evolving landscape of our industry, it’s clear that proactive management of cybersecurity is a necessity to protect critical infrastructure and data.
Jennifer Obertino, global energy practice lead, AECOM
Business
Low-carbon developers will need to treat cybersecurity as a board-level responsibility. This will require new capital investment, expanded capabilities and consistent risk reviews. Operational asset assessments and end-to-end supply chain audits are now essential. Companies must adopt mandatory vendor risk assessments, zero-trust access controls and ongoing security audits. Failure to treat cyber risk as a strategic priority may directly affect business continuity and financial performance.
Investors
As capital flows into low-carbon development, investors should seek to embed cybersecurity as a core metric in their due diligence.
Cyber maturity should be evaluated alongside technical innovation and leadership strength. Operational resilience testing and digital attack simulations must become standard. Companies without full NIS 2.0 compliance may find themselves classified as high-risk, no matter their growth story or green credentials.
In a more complex and volatile geopolitical world, renewable energy companies need to focus on and escalate the importance of cyber resilience. The companies that do so will improve operational performance and profitability, while simultaneously helping to address energy security.
If we don’t secure the future of energy, we risk powering progress with vulnerability. Cyber must not be the afterthought of sustainability: it must be its backbone.
Rafael Narezzi, founder, Cyber Energia
For more information contact our global energy advisory lead, Adrian Del Maestro.






